Memory is required in computers to store data and instructions. Memory is physically organized as a large number of cells that are capable of storing one bit each. Logically they are organized as groups of bits called words that are assigned an address. Data and instructions are accessed through these memory address. The speed with which these memory addresses can be accessed determines the cost of the memory. Faster the memory speed, higher the price.
Computer memory can be said to be organized in a hierarchical way where memory with the fastest access speeds and highest costs lies at the top whereas those with lowest speeds and hence lowest costs lie at the bottom. Based on this criteria memory is of two types – primary and secondary. Here we will look at primary memory in detail.
The main features of primary memory, which distinguish it from secondary memory are −
- It is accessed directly by the processor
- It is the fastest memory available
- Each word is stored as well as
- It is volatile, i.e. its contents are lost once power is switched off
As primary memory is expensive, technologies are developed to optimize its use. These are broad types of primary memory available.
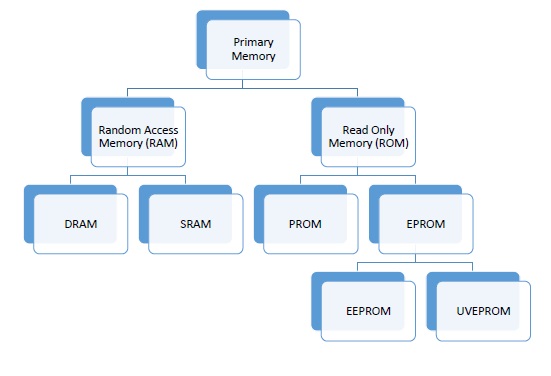
RAM
RAM stands for Random Access Memory. The processor accesses all memory addresses directly, irrespective of word length, making storage and retrieval fast. RAM is the fastest memory available and hence most expensive. These two factors imply that RAM is available in very small quantities of up to 1GB. RAM is volatile but my be of any of these two types
DRAM (Dynamic RAM)
Each memory cell in a DRAM is made of one transistor and one capacitor, which store one bit of data. However, this cell starts losing its charge and hence data stored in less than thousandth of a second. So it needs to be refreshed thousand times a second, which takes up processor time. However, due to small size of each cell, one DRAM can have large number of cells. Primary memory of most of the personal computers is made of DRAM.
SRAM (SRAM)
Each cell in SRAM is made of a flip flop that stores one bit. It retains its bit till the power supply is on and doesn’t need to be refreshed like DRAM. It also has shorter read-write cycles as compared to DRAM. SRAM is used in specialized applications.
ROM
ROM stands for Read Only Memory. As the name suggests, ROM can only be read by the processor. New data cannot be written into ROM. Data to be stored into ROM is written during the manufacturing phase itself. They contain data that does not need to be altered, like booting sequence of a computer or algorithmic tables for mathematical applications. ROM is slower and hence cheaper than RAM. It retains its data even when power is switched off, i.e. it is non-volatile. ROM cannot be altered the way RAM can be but technologies are available to program these types of ROMs −
PROM (Programmable ROM)
PROM can be programmed using a special hardware device called PROM programmer or PROM burner.
EPROM (Erasable Programmable ROM)
EPROM can be erased and then programmed using special electrical signals or UV rays. EPROMs that can be erased using UV rays are called UVEPROM and those that can be erased using electrical signals are called EEPROM. However, handling electric signals is easier and safer than UV rays.
Cache Memory
Small piece of high speed volatile memory available to the processor for fast processing is called cache memory. Cache may be a reserved portion of main memory, another chip on CPU or an independent high speed storage device. Cache memory is made of fast speed SRAMs. The process of keeping some data and instructions in cache memory for faster access is called caching. Caching is done when a set of data or instructions is accesses again and again.
Whenever the processor needs any piece of data or instructions, it checks the cache first. If it is unavailable there, then the main memory and finally secondary memory is accessed. As cache has very high speed, time spent in accessing it every time is negligible as compared to time saved if data indeed is in the cache. Finding data or instruction in cache is called cache hit.