| Short-cut keys Functions | |
|---|---|
| Commonly Used Short-cut Keys | |
| F1 | Universal help (for any sort of program). |
| Alt + F | File menu options in current program. |
| Alt + E | Edits options in current program. |
| Ctrl + A | Selects all text. |
| Ctrl + X | Cuts the selected item. |
| Ctrl + C | Copies the selected item. |
| Ctrl + V | Pastes copied item. |
| Home | Takes the user to the beginning of the current line. |
| End | Takes the user to the end of the current line. |
| Ctrl + Home | Takes the user to the beginning of the document. |
| Ctrl + End | Takes the user to the end of the document. |
| Shift + Home | Highlights from the current place to the beginning of line. |
| Shift + End | Highlights from the current place to the end of line. |
| Microsoft Windows Shortcut Keys | |
| Ctrl + F4 | Closes window in program. |
| Alt + F4 | Closes current open program. |
| F2 | Renames the selected icon. |
| F3 | Start find from desktop. |
| F4 | Opens the drive selection when browsing. |
| F5 | Refreshes contents. |
| Alt + Tab | Switches from one open application to another open application. |
| Alt + Shift + Tab | Switches backwards between open applications. |
| Alt + Print Screen | Creates screen shot for current program. |
| Ctrl + Alt + Del. | Opens windows task manager/reboot. |
| Ctrl + Esc | Brings up start menu. |
| Alt + Esc | Switches between applications on taskbar. |
| Ctrl + Plus (+) Key | Automatically adjusts widths of all columns in Windows Explorer. |
| Alt + Enter | Opens properties window of selected icon or program. |
| Shift + F10 | Simulates right-click on selected item. |
| Shift + Del | Deletes selected programs/files permanently. |
| Holding Shift During Boot-up | Enables boot safe mode or bypass system files. |
| Ctrl + N | Starts a new note. |
| Ctrl + O | Opens a recently used note. |
| Ctrl + S | Saves changes to a note. |
| Ctrl + P | Prints a note. |
| Alt + F4 | Closes a note and its Journal window. |
| Ctrl + Z | Helps Undo a change. |
| Ctrl + Y | Helps Redo a change. |
| Ctrl + A | Selects all items on a page. |
| Ctrl + X | Cuts a selection. |
| Ctrl + C | Copies a selection to the Clipboard. |
| Ctrl + V | Pastes a selection from the Clipboard. |
| Esc | Cancels a selection. |
| Ctrl + F | Start a search tool. |
| Ctrl + Shift + C | Display a shortcut menu for column headings in a note list. |
| Microsoft Word Shortcut Keys | |
| Ctrl + N | Creates a new document. |
| Ctrl + O | Opens an existing document. |
| Ctrl + S | Saves changes to a document. |
| F12 | Saves the document as a new file. |
| Ctrl + P | Prints a document. |
| Ctrl + Z | Helps Undo a change. |
| Ctrl + Y | Helps Redo a change. |
| Ctrl + A | Selects the whole document. |
| Ctrl + X | Helps cut a selection |
| Ctrl + C | Copies a selection to the Clipboard. |
| Ctrl + V | Pastes a selection from the Clipboard. |
| Ctrl + B | Makes selected text bold. |
| Ctrl + I | Italicizes selected text. |
| Ctrl + U | Underlines selected texts. |
| Ctrl + L | Aligns text left. |
| Ctrl + R | Aligns text right. |
| Ctrl + E | Aligns text center. |
| Ctrl + J | Helps justify text. |
| Ctrl + 1 | Sets single line spacing. |
| Ctrl + 2 | Sets double line spacing. |
| Ctrl + 5 | Sets line spacing to 1.5. |
| Ctrl + Shift + A | Changes characters to all capitals. |
| Ctrl + D | Inserts a Microsoft Paint drawing. |
| Ctrl + F | Finds text |
| Ctrl + Home | Moves to the beginning of the document. |
| Ctrl + End | Moves to the end of the document. |
Home of Computer Training, & Entertainment. To Inspired and Develop the Society in a Digital World.
Sunday, October 30, 2022
Shortcut Keys
Development
In this chapter, we will discuss the development in Computer Science chronologically.
The following table lists down the development −
| Year | Development |
|---|---|
| 1959 | Transistors: IBM 7090; IBM 1401 |
| 1962 | NPN transistor |
| 1963 | Mouse; CMOS patented |
| 1964 | CDC 6600; IBM Data Cell Drive |
| 1966 | Integrated circuits: HP 2116A |
| 1966 | Apollo Guidance Computer |
| 1969 | Honeywell 316 |
| 1971 | 8" floppy disk; ILLIAC IV |
| 1973 | Micral first microprocessor PC |
| 1980 | Sinclair ZX80, Seagate hard disk drive |
| 1981 | IBM PC, Acorn BBC Micro |
| 1983 | Apple Lisa; 3.5" floppy |
| 1984 | Apple Mac; Apple Lisa 2 |
| 1988 | Dell |
| 1989 | NeXT |
| 1991 | Apple Switches to PowerPC |
| 1992 | HP 95LX; Palmtop PC |
| 1995 | IBM Deep Blue chess computer |
| 1996 | USB 1.0 |
| 1997 | Compaq buys Tandem; CD-RW |
| 1998 | iMac |
| 2000 | USB 2 |
| 2001 | Apple iPod |
| 2005 | Mac Mini |
| 2006 | Apple transition to Intel |
| 2007 | iPhone 1 |
| 2008 | USB 3.0 |
| 2010 | Apple iPad |
| 2012 | IBM zEnterprise System |
Abbreviations
In this chapter, we will discuss the different abbreviations in Computer Science. The following table lists down those abbreviations −
| Abbreviation | Full-name |
|---|---|
| A/D | Analog-to-Digital |
| ABC | Atanasoff Berry Computer |
| ACM | Association for Computing Machinery |
| AI | Artificial Intelligence |
| ALGOL | Algorithic Language |
| ALU | Arithmetic Logic Unit |
| AMD | Advanced Micro Devices |
| APRANET | Advanced Research Project Agency Network |
| ASCII | American Standard Code for Information Interchange |
| BASIC | Beginners All-purpose Symbolic Instruction Code |
| BCD | Binary Coded Decimal |
| BIOS | Basic Inpute Output System |
| BIPS | Billions of Instructions Per Second |
| BPI | Bytes Per Inch |
| CAD | Computer Aided Design |
| CAE | Computer Aided Engineering |
| CAN | Campus Area Network |
| CASE | Computer Aided Software Engineering |
| CD | Compact Disk |
| CDC | Control Data Corporation |
| CD-R | CD-Recordable |
| CD-ROM | Compact Disk Read Only Memory |
| CD-RW | CD Read/Write |
| CL | Command Language |
| CLI | Command Line Interface |
| COBOL | Common Business Oriented |
| CODASYL | Conference On Data Systems |
| CPU | Central Processing Unit |
| CRT | Cathode Ray Tube |
| D/A | Digital-to-Analog |
| DAT | Digital Audio Tape |
| DBMS | Data Base Management System |
| DBS | Demand Based Switching |
| DDL | Data Definition Language |
| DDS | Digital Data Storage |
| DEC | Digital Equipment Corporation |
| DMA | Direct Memory Access |
| DNA | Digital Network Architecture |
| DPI | Dots Per Inch |
| DRAM | Dynamic RAM |
| DSN | Distributed Systems Network |
| DTS | Digital Theater System |
| DVD | Digital Video/Versatile Disk |
| EBCDIC | Extended Binary Coded Decimal Interchange Code |
| EDSAC | Electronic Delay Storage Automatic Calculator |
| EDVAC | Electronic Discrete Variable Automatic Calculator |
| EFM | Eight-to-Fourteen Modulation |
| ENIAC | Electronic Numerical Integrator And Calculator |
| EPG | Electronic Programming Guide |
| EPIC | Explicitly Parallel Instruction Computing |
| EPROM | Erasable Programmable Read-Only Memory |
| FAT | File Allocation Table |
| FDM | Frequency Division Multiplexing |
| FEP | Front End Processor |
| FLOPS | Floating Point Operations Per Second |
| FM | Frequency Modulation |
| FMS | File Management System |
| FORTRAN | FORmula TRANslation |
| FSK | Frequency Shift Keying |
| FTP | File Transfer Protocol |
| GB | Giga Bytes |
| GFLOPS | Giga FLOPS |
| GHz | Giga Hertz |
| GNU | Gnu Not Unix |
| GPRS | General Packet Radio Service |
| GSM | Global System for Mobile communication |
| GUI | Graphical User Interface |
| HP | Hewlett Packard |
| HSS | Hierarchical Storage System |
| HTML | HyperText Markup Language |
| HTTP | HyperText Transport Protocol |
| IBM | International Business Machine |
| IC | Integrated Circuit |
| IDN | Integrated Digital Networks |
| IP | Internet Protocol |
| IrDA | Infrared Data Association |
| ISDN | Integrated Services Digital Network |
| ISP | Internet Service Provider |
| JPEG | Joint Photographic Experts Group |
| JRE | Java Runtime Engine |
| JSP | Java Server Pages |
| KB | Kilo Bytes |
| KHz | Kilo Hertz |
| LAN | Local Area Network |
| LCD | Liquid Crystal Display |
| LED | Light Emitting Diode |
| LPM | Line Per Minute |
| LSI | Large Scael Integration |
| MAN | Metropolitan Area Network |
| MAR | Memory Address Register |
| MB | Mega Bytes |
| MBR | Memory Buffer Register |
| MHz | Mega Hertz |
| MIDI | Musical Instrument Digital Interface |
| MIPS | Millions of Instructions Per Second |
| MNP | Microcom Network Protocol |
| MPEG | Moving Pictures Experts Group |
| MS-DOS | MicroSoft Disk Operating System |
| MVT | Multiprogramming with Variable Tasks |
| NIC | Network Interface Card |
| NICNET | National Informatics Center NETwork |
| NOS | Network Operating System |
| OCR | Optical Character Recognition |
| OMR | Optical Mark Reader |
| OS | Operating System |
| OSI | Open System Interconnection |
| OSS | Open Source Software |
| PAN | Personal Area Network |
| PC | Personal Computer |
| Portable Document Format | |
| PDL | Program Design Language |
| PDP | Program Data Processor |
| PIP | Peripheral Interchange Program |
| PROM | Programmable Read-Only Memory |
| QoS | Quality of Service |
| RAM | Random Access Memory |
| ROM | Read Only Memory |
| SDLC | Software Development Life Cycle |
| SEQUEL | Structured English QUEry Language |
| SGML | Syntax for Generalized Markup Language |
| SIMM | Single In-line Memory Module |
| SNA | Systems Network Architecture |
| SNOBOL | StriNg Oriented and symBOlic Language |
| SQL | Structured Query Language |
| SRAM | Static RAM |
| SSI | Small Scale Integration |
| TB | Tera Bytes |
| TCP | Transport Control Protocol |
| TDM | Time Division Multiplexing |
| UDP | User Datagram Protocol |
| ULSI | Ultra Large Scale Integration |
| UPC | Universal Product Code |
| URL | Uniform Resource Locator |
| USB | Universal Serial Bus |
| UTF | Unicode Transformation Format |
| VAN | Value Added Network |
| VCR | Video Cassette Recorder |
| VDT | Video Display Terminal |
| VGA | Video Graphics Array |
| VOD | Video-On-Demand |
| VoIP | Voice over Internet Protocol |
| VSAT | Very Small Aperture Terminal |
| WAN | Wide Area Network |
| WAP | Wireless Application Protocol |
| WiMAX | Worldwide Interoperability for Microwave Access |
| WLAN | Wireless Local Area Network |
| WLL | Wireless Local Loop |
| WORM | Write Once Read Many |
| WWW | World Wide Web |
| XHTML | eXtensible HyperText Markup Language |
| XML | eXtensible Markup Language |
| X.400 | Electronic Mail Protocol |
| X.500 | Directory Server Protocol |
Virus
A virus is a computer code or program, which is capable of affecting your computer data badly by corrupting or destroying them.
Computer virus has the tendency to make its duplicate copies at a swift pace, and also spread it across every folder and damage the data of your computer system.
A computer virus is actually a malicious software program or "malware" that, when infecting your system, replicates itself by modifying other computer programs and inserting its own code.

Infected computer programs may include data files, or even the "boot" sector of the hard drive.
Types of Virus
Following are the major types of computer virus −
Worms
This is a computer program that replicates itself at a swift pace. Unlike a computer virus, it is self-contained and hence does not need to be part of another program to propagate itself.
Trojan Horse
A Trojan Horse is also a sort of destructive program that remains disguised in a normal software program. It is not exactly a virus, as it cannot replicate itself. However, there is possibility that virus program may remain concealed in the Trojan Horse.
Bombs
It is similar to Trojan Horse, but Logic bombs have some specialty; these include a timing device and hence it will go off only at a particular date and time.
How Does Virus Affect?
Let us discuss in what ways a virus can affect your computer system. The ways are mentioned below −
- By downloading files from the Internet.
- During the removable of media or drives.
- Through pen drive.
- Through e-mail attachments.
- Through unpatched software & services.
- Through unprotected or poor administrator passwords.
Impact of Virus
Let us now see the impact of virus on your computer system −
- Disrupts the normal functionality of respective computer system.
- Disrupts system network use.
- Modifies configuration setting of the system.
- Destructs data.
- Disrupts computer network resources.
- Destructs of confidential data.
Virus Detection
The most fundamental method of detection of virus is to check the functionality of your computer system; a virus affected computer does not take command properly.
However, if there is antivirus software in your computer system, then it can easily check programs and files on a system for virus signatures.
Virus Preventive Measures
Let us now see the different virus preventive measures. A computer system can be protected from virus through the following −
- Installation of an effective antivirus software.
- Patching up the operating system.
- Patching up the client software.
- Putting highly secured Passwords.
- Use of Firewalls.
Most Effective Antivirus
Following are the most popular and effective antivirus from which you can choose one for your personal computer −
- McAfee Antivirus Plus
- Symantec Norton Antivirus
- Avast Pro Antivirus
- Bitdefender Antivirus Plus
- Kaspersky Anti-Virus
- Avira Antivirus
- Webroot Secure Anywhere Antivirus
- Emsisoft Anti-Malware
- Quick Heal Antivirus
- ESET NOD32 Antivirus
Threat
Threat in a computer system is a possible danger that might put your data security on stake. The damage is at times irreparable.

Definition
As defined by the National Information Assurance Glossary −
“Any circumstance or event with the potential to adversely impact an IS through unauthorized access, destruction, disclosure, modification of data, and/or denial of service.”
A computer threat can be "intentional" such as hacking or "accidental" such as malfunctioning of or physical damage.
Types of Threat
Following are the most common types of computer threats −
Physical damage − It includes fire, water, pollution, etc.
Natural events − It includes climatic, earthquake, volcanic activity, etc.
Loss of services − It includes electrical power, air conditioning, telecommunication, etc.
Technical failures − It includes problems in equipment, software, capacity saturation, etc.
Deliberate type − It includes spying, illegal processing of data, etc.
Some other threats include error in use, abuse of rights, denial of actions, eavesdropping, theft of media, retrieval of discarded materials, etc.
Sources of Threat
The possible sources of a computer threat may be −
Internal − It includes employees, partners, contractors (and vendors).
External − It includes cyber-criminals (professional hackers), spies, non-professional hackers, activists, malware (virus/worm/etc.), etc.
Common Terms
Following are the common terms frequently used to define computer threat −
Virus Threats
A computer virus is a program designed to disrupt the normal functioning of the computer without the permission of the user.
Spyware Threats
Spyware is a computer program that monitors user’s online activities or installs programs without user’s consent for profit or theft of personal information.
Hackers
Hackers are programmers who put others on threats for their personal gain by breaking into computer systems with the purpose to steal, change or destroy information.
Phishing Threats
It is an illegal activity through which phishers attempt to steal sensitive financial or personal data by means of fraudulent email or instant messages.
How to Secure Your Computer System from Threats?
Following are the significant tips through which you can protect your system from different types of threat −
- Install, use, and keep updated Anti-Virus in your system.
- Install, use, and keep updated a Firewall Program.
- Always take backups of your important Files and Folders.
- Use Strong and Typical Passwords.
- Take precaution especially when Downloading and Installing Programs.
- Install, use, and keep updated a File Encryption Program.
- Take precaution especially when Reading Email with Attachments.
- Keep your Children aware of Internet threats and safe browsing.
Monday, October 24, 2022
Security
Advancement of computer technology has radically changed the world; resultantly, most of the works whether it is matter of nation’s security system or buying a shoe online everything depends on computer.
Such increased dependency also raises the issue of security, as most of the data is now stored in the computer system.

Your computer systems store various sorts of data and hence if it is not secured, then you might be in for a big trouble.
Why Do We Computer Security?
Let us now see why do we need Computer security. It is required for the following major reasons −
To prevent damage of the hardware.
To prevent theft or damage of the installed software.
To prevent theft or damage of stored data and information.
To prevent the disruption of service.
Likewise, security system keeps the computer system safe by protecting the installed software and the stored data (information).
Protection of Data and Information
Following are the important steps to protect data −
- Make backup of all your important files.
- Keep your system virus by using anti-virus software.
- Keep updating your computer system.
- Run disk defragmenter and disk cleanup on certain interval of time.
- Use a firewall.
- Use anti-spyware software.
Further, if you use internet, then you need to take greater precaution. Consider the following points to understand the precautions that need to be taken −
Do not click on any link that you don’t know (as it may be dangerous for your computer - virus attack).
Do not open unauthorized an unlawful website (it may damage your computer system).
Do not download unsolicited data from unknown website.
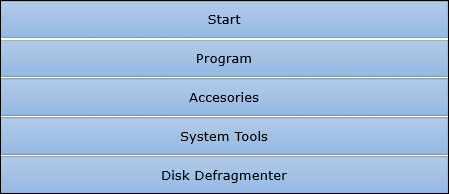
What is Defragmentation?
Frequent saving and deleting of file (data) from the hard disk creates problems in performance and also reduce the space; therefore, defragmentation again clean-up the drive and restore the system to run smoothly.
Following are the simple steps of defragmentation −
Disk Cleanup
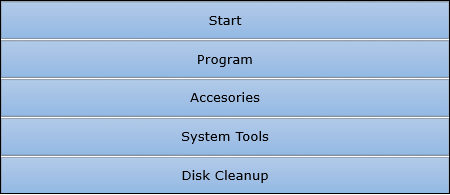
While browsing websites (on internet), many of the files get stored in the hard disk automatically (actually these stored files later help to reopen the website faster); besides some other cookies also get stored in the hard disk. All these stored files create problem along with eating space.
So, disk cleanup process cleans all these files and releases the space occupied by these unwanted files.
Following are the simple steps of disk cleanup −
Multimedia
In this chapter, we will discuss how the Computer Multimedia works. If a system presents, some information through more than two media, it is known as multimedia. For example, TV presents audio and video; book presents text, image, and graphs, computer, etc.
The information presented through multimedia has better quality and capability, as it can be understood easily.

The advanced computer system is a great example of modern multimedia.
Literal Meaning of Multimedia
In this section, we will understand the literal meaning of multimedia.
Multi − it means more than one
Medium − it is singular and it means intermediary or mean
Media − it is plural and it means conveying the information
Likewise, Multimedia is the field of Computer Science that integrates different forms of information and represents in the form of audio, video, and animation along with the traditional media, i.e., text, graphics/drawings, images, etc.
Multimedia Computer System
Multimedia computer system has high capacity to integrate different media including text, image, graphics, audio, and video.
The multimedia computer system stores, represents, processes, manipulates, and makes available to users.
Significant Features of Multimedia Computer System
Following are the major features multimedia computer system −
Its Central Processing Unit (CPU) is very fast, as it needs to process large amount of data.
It has huge storage capacity.
It has huge memory power that helps in running heavy data programs.
It has high capacity graphic card that helps in displaying graphics, animation, video, etc.
The sound system makes it easy to listen to audio.
With all these features (discussed above), a computer system is known as high end multimedia computer system.
However, all the features listed above are not essentially required for every multimedia computer system, but rather the features of a multimedia computer system are configured as per the need of respective user.
Multimedia Components
Following are the major components of a multimedia computer system −
Text
It contains alphanumeric and some other special characters. Keyboard is usually used for input of text; however, there are some internal (inbuilt) features to include such text.
Graphics
It is technology to generate, represent, process, manipulate, and display pictures. It is one of the most important components of multimedia application. The development of graphics is supported by a different software.
Animation
Computer animation is a modern technology, which helps in creating, developing, sequencing, and displaying a set of images (technically known as ‘frames’). Animation gives visual effects or motion very similar to that of a video file (see image given below).

Audio
This technology records, synthesizes, and plays audio (sound). There are many learning courses and different instructions that can be delivered through this medium appropriately.
Video
This technology records, synthesizes, and displays images (known as frames) in such sequences (at a fixed speed) that makes the creation appear as moving; this is how we see a completely developed video. In order to watch a video without any interruption, video device must display 25 to 30 frames/second.
Multimedia Application
Let us now see the different fields where multimedia is applied. The fields are described in brief below −
Presentation
With the help of multimedia, presentation can be made effective.
E-books
Today, books are digitized and easily available on the Internet.
Digital Library
The need to be physically present at a library is no more necessary. Libraries can be accessed from the Internet also. Digitization has helped libraries to come to this level of development.
E-learning
Today, most of the institutions (public as well as private both) are using such technology to education people.
Movie making
Most of the special effects that we see in any movie, is only because of multimedia technology.
Video games
Video games are one of the most interesting creations of multimedia technology. Video games fascinate not only the children but adults too.
Animated films
Along with video games, animated film is another great source of entertainment for children.
Multimedia conferencing
People can arrange personal as well as business meetings online with the help of multimedia conferencing technology.
E-shopping
Multimedia technology has created a virtual arena for the e-commerce.
SYSTEM SOFTWARE
As you know, system software acts as an interface for the underlying hardware system. Here we will discuss some important system...

-
Zoom Slider By default, everything on screen is displayed at 100% in MS Excel. You can change the zoom percentage from 10% (tiny...
-
Slide master is simple way of applying changes to the entire slide. Every presentation has at least one slide master, but you ca...
-
Let us see how to open workbook from excel in the below mentioned steps. Step 1 − Click the File Menu as shown below. You can see the Op...






